You are here
Hi all,
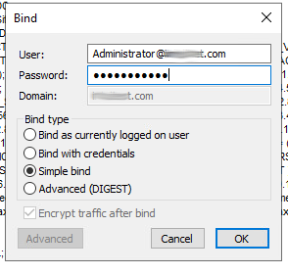
I have set up a Windows Server 2019 Primary Domain Controller on my test network. I ran through and resolved all of the issues found with DCDiag and the Best Practices Analyzer. The DC is discoverable on my network. On the 2019 DC I ran ldp.exe and successfully connected both with and without SSL. At first, I was not able to perform a "simple bind" until I read that I needed to append the username with @domain.tld (see attached image). Once I did that, I no longer received the error. I also found that I can successfully bind with no credentials - anonymously.
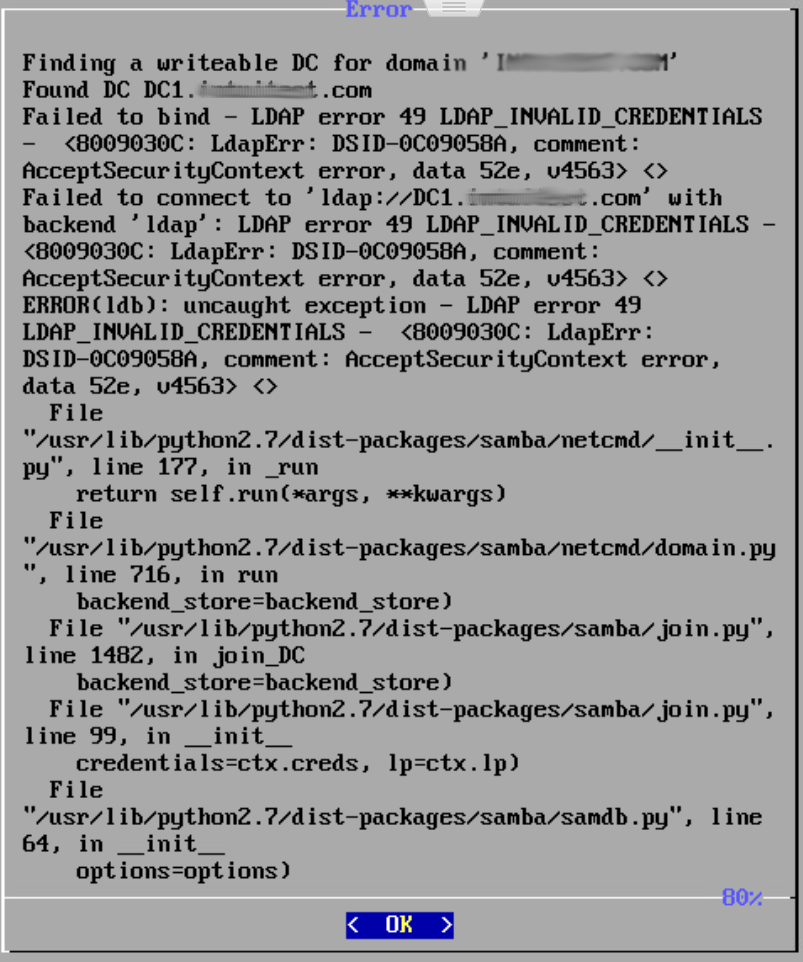
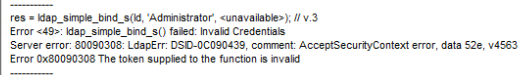
I booted up the Turnkey Domain Controller that was downloaded a few days ago, entered the root password, realm, NetBIOS name and Administrator password and hit OK. I was promptly presented with an error (see attahced image). The message stated that it found my DC but "Failed to bind - LDAP error 49 LDAP_INVALID_Credentials...". I assure you, they are not. Since there is no way for me to do append the username with the domain during the TK DC installation, how do I join it to my domain? Do I create a "new" domain and then demote it, or is there something else I should be doing? The only other option I can think of is to do a clean install using Debian/Ubuntu server and follow the instructions at Samba.org to join a Windows DC. I'd rather just boot up the TK DC. I've been researching this for about 16 hours now and have come up dry. Any help is greatly appreciated.
Thank you,
Troy
My guess is lack of support for current AD schema versions
Samba (the underlying software that TurnKey DC appliance uses) is not 100% compatible with more recent versions of MS AD. It's reverse engineered and MS don't share all their secrets, and even if they did, the Samba team would still be somewhat behind.
The version of Samba (v4.9) that TurnKey currently has has "experimental" support for AD schema version 69 - i.e. Win Server 2012r2 (source). That doesn't mean that you can't use versions of MS Server newer than 2012r2, but it does mean that you need to be using AD schema version 69 or lower (i.e. configure it for legacy AD support).
As such, whilst Samba can be an AD replacement, joining an existing domain (that is running on MS Server) is generally not going to be a smooth ride. The "join existing domain" is more intended to join one Samba AD DC to another Samba AD DC.
Despite my above notes, you may still be able to get it work, at least at an acceptable level, if not optimal. You'll likely need to (re)configure it yourself via the CLI though, rather than using our wrapper scripts that simplify the process). Here's a doc page that may be of assistance?
I have limited experience with recent versions of Windows - I "converted" to Linux nearly 10 years ago and the last Win Server I administered was 2012r2. Regardless though, I'm more than happy to do my best to help if I can...
Thank you
Thanks Jeremy. That makes perfect sense. I will give the CLI option a try.
Troy
FYI, here's the doc link I probably should have posted...
You're most welcome - and I'd love to hear how you go. If possible it'd be great if you could provide feedback on what works or doesn't and (assuming you can get it working ok) it'd be awesome if you could share the steps you take. Perhaps we can use your experience to improve our scripts?
And also, the doc link that I probably should have given you is this one: Setting up Samba as a Domain Member, or perhaps Joining a Samba DC to an Existing Active Directory (they seem very similar...). The one I posted previously was regarding creation of a Samba AD DC. Whilst it might be useful to some, it's not what you're trying to achieve and I think that part of our setup is pretty solid. One other page that might be of interest too, is the Samba AD DC Troubleshooting page.
Good luck with it all, and please do ask if there is anything more I can help with. I look forward to hearing how it goes.
Schema
Hi Jeremy,
Using a Powershell command, I dropped the schema down to Win 2008 but it didn't seem to work with that either. Thankfully, I have documented my setup. I am going to re-install Server 2019 and set it to a lower schema during installation. I beleive I originally chose 2012, but that is not part of what I documented. It will be on this next round. I will let you know what I find and would be happy to share my documentation.
I appreciate the links. Over the last month or two of experimentation, I've become familiar with them. I've been using Linux for many years but still consider myself a novice, as I have mostly shied away from the command line and dealt mostly with the GUI. Setting up a Samba DC seems fairly cut and dried but I always seem to run into brick walls I can't get through. A fresh install of Samba as a DC just never seemed to work for me, hence the Windows license. If I can get it to work as a secondary DC, it would save us some money. My boss is patient, so I will keep plugging away at it.
Thanks again for your help. I will post an update in the next day or two.
Cheers,
Troy
Good luck with it.
If you choose "2012" schema (i.e. not "2012r2") then you should definitely be fine (and at the very least rule that out as the issue). AFAIK, even using the "2021r2" schema should be fine as far as the basics go.
Whilst the set up is relatively straight forward, there are a few details that have nuance (and different options that may apply in different scenarios). Although really the basics of joining, should mostly "just work" I would expect.
If you continue to have issues, then I suggest consulting the experts over on the samba@lists.samba.org mailing list. Hopefully someone there might be able to help out?
If you do that, please be aware that (as I've likely mentioned) TurnKey (v16.x) is based on Debian (10/Buster) and has Samba v4.9 (installed from Debian repos). if you're not already, be sure to nuke the previous config before retrying. Assuming that you're doing that, then you should be using default Debian config. Regarding Samba specifically, we provide some "addons" (webmin module - that has limited value with AD; and our setup scripts which didn't work for you anyway...),s o clean CLI config should be same as if you were using vanilla Debian.
Dropped Forest and Domain Levels
Hi Jeremy,
As always, thanks for the info. I will check out that list.
Yesterday, I restored my ADDC to an earlier snapshot from just after installation and updates, and before the Active Directory and DNS roles were added. I then went through adding the AD and DNS roles. During the steps to promote the server to a domain controller, I was given the option to set the forest and domain levels. I chose Server 2008 R2, as that's what Zentyal requires. Btw, I can't get that to join properly either. A few minutes ago I created a new vm using the TK DC ova file. I attempted to join it to my dc and got the same error. I'm going to play around with it a bit more. If I still can't get it to work, I will reach out to the folks on that other list.
Troy
I've just had a thought....
I'm not sure if I mentioned this before, but Kerberos authentication (as used by Windows/Samba AD) is time-sensitive (IIRC clocks must be within 20 seconds of each other). So if the clocks are out of sync, then that will cause issues...
Perhaps I already mentioned it, or perhaps you've already thought of it, but perhaps that's an issue?
I gave up
I gave up on Samba and Zentyal after messing with it for a week or two. Windows Server is expensive but it works and I know how to use it. I hope you can get your system working.
Add new comment